Cyber risk remains a major existential threat for organisations, public institutions, supply chains and critical infrastructure as accelerated levels of digitalisation across businesses, economies and societies continue apace. With many organisations either oblivious to the dangers, or worse, complacent about their threat exposure, at a time when internet use, connected devices and IoT-networked sensors are experiencing massive growth, responding to the threat with effective, layered cyber deterrence should be initiated and led at boardroom level with urgency.
As IBM’s chairman was warning as far back as 2015, “cybercrime, by definition, is the greatest threat to every profession, every industry, every company in the world”.
Cybercrime in brief: a snapshot
Global premiums for cyber insurance are predicted to grow from US$ 9.2 billion in 2022 to US$22 billion by 2025, with some estimates suggesting they could reach over US$ 60 billion by 2029. This may come as no surprise when you consider that the economic hit from cybercrime was around US$ 6 trillion in 2021, and by 2025, Cisco’s ‘2022 Cybersecurity Almanac’ forecasts that the reported cost of cybercrime will exceed a staggering US$ 10 trillion per annum, the equivalent of around 10% of global GDP in 2025. It is estimated, however, that as many as 90% of cybercrimes go unreported, partly because of extremely poor detection and prosecution rates.
According to Accenture’s ‘State of Cybersecurity Resilience 2021’ report, the average number of attacks per company reached 270 last year, with large UK organisations experiencing triple the global average of attempted cyber-attacks. The average total cost of data breaches in 2021 exceeded US$ 4 million, with breaches in the US the costliest at an average of more than US$ 9 million, followed by the Middle East at over US$ 7 million. Data breaches in the healthcare industry were the most expensive, at more than US$ 10 million on average.
As reported by MunichRe, one cyber-criminal group known as Conti extorted approximately US$ 180 million in 2021 alone. Yet many organisations are complacent and even over-confident when it comes to cyber risk, with over 40% of US and UK executives declaring themselves “very prepared” to meet the cyber threat, according to the Beazley Group. Some of today’s business leaders risk becoming blinkered from the developing threats of the future by threat saturation today – a plethora of existing risks posed by economically motivated cyber criminals, activist hackers and geopolitical instability is in danger of blinding them to future risk exposure.

With many businesses still unaware of the risks posed by a lack of employee security awareness – over 80% of data breaches involve human error – it is worth considering some of today’s major cyber issues and detailing the steps businesses can take to improve insurability and protect themselves from existential threats. We will also identify some future trends in this area.
Costs, threats & target exposure
Costs
As we have seen above, cybercrime costs will top US$ 10 trillion, or 10% of global GDP, within a few years. With the sheer scale of the problem and its potential damages massively underrated, the potential economic hit from cybercrime could by-pass climate change as the single biggest threat to global GDP.
Given the pervading narrative on potential climate-change losses, that may seem hard to comprehend, but the figures speak for themselves. Indeed, as Cybersecurity Ventures reports, cybercrime is already, “exponentially larger than the damage inflicted from natural disasters”.
If the World Economic Forum (WEF) predictions and the Paris climate targets are correct and global warming is limited to <2⁰C – at a cost of 4.2% GDP losses,– cybercrime (constrained to 2025 levels at 5% of global GDP) could end up costing more than climate change by 2050, and emerge as by far and away the number-one threat to global prosperity in the 21st Century.
Threats
What are today’s threats, where do tomorrow’s threats lie, and what damage can they inflict? Cyber attacks are becoming more sophisticated in their design and more insidious in their deployment; worryingly, the source and scope of attacks has also broadened significantly, according to Aon.
Research shows that over 90% of cyber-attacks start as so-called ‘spear phishing’ emails. Spear phishing is an insidious attack method by which individuals within an organisation are targeted through their social media presence. This allows attackers to tailor phishing email campaigns – in which users are tricked or lulled into clicking a link or providing sensitive data – directed specifically at those individuals who are, given the high levels of penetration, clearly unaware of the dangers.
Malware such as ransomware, a particular type of economic cyber-attack that demands payment for decryption keys to free up an organisation’s hijacked IT infrastructure, hardware or software, is the number-one cyber threat across the board, according to MunichRe. It has become so prevalent, professional and ruinous that French insurer AXA announced in May that it would stop covering ransomware payments in France.
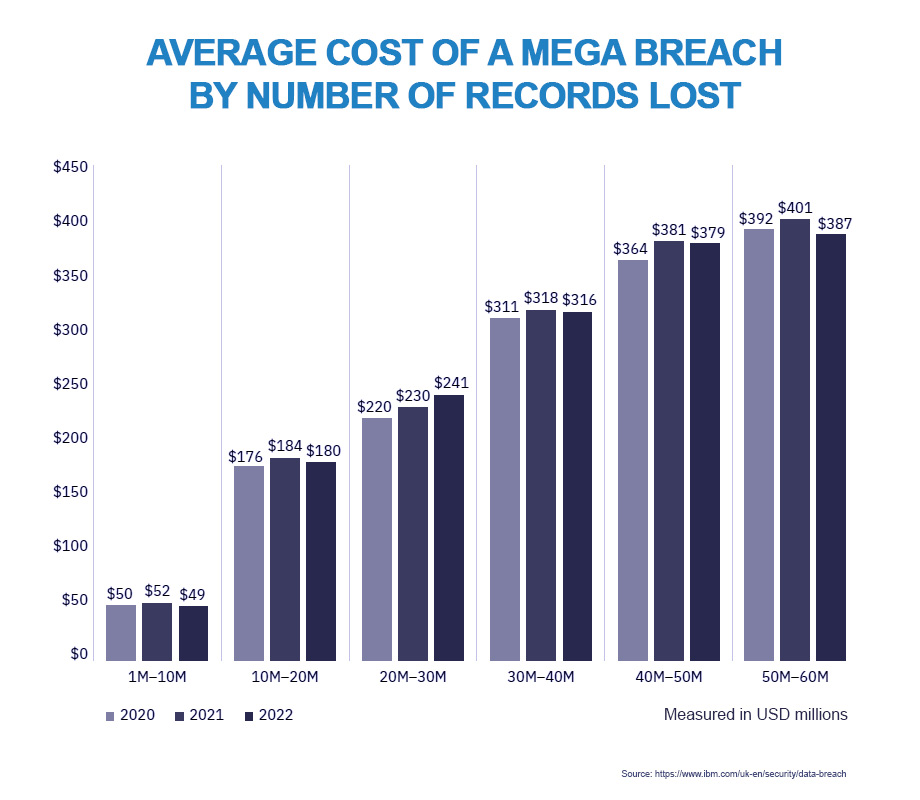
It was widely reported at the time that the ransomware attack in 2021 on the US Colonial Pipeline, a 5,500-mile pipeline that delivers refined oil products across the US from Texas to New Jersey, extorted a ransom of US$ 4.4 million-equivalent in bitcoin to restore data and resume operations, although the ransom was later partially recovered. The attack, in which hackers breached its systems through exposed password reuse on a VPN and briefly paralysed infrastructure up and down the US East Coast, was not even the costliest attack of 2021 – US insurance firm CNA Financial paid out around US$ 40 million after falling victim to a ransom group known as Phoenix, and the Republic of Ireland’s public healthcare system suffered US$ 600 million in damage after a ransomware attack. Cybersecurity Ventures reports that a ransomware attack happened every 11 seconds on average in 2021 at an average cost of US$ 118,000 per successful attack, and attacks are likely to rise to one every two seconds by 2031. According to MunichRe, “criminal extortion in cyberspace is becoming ever more professional and complex and is often carried out by agile, coordinated criminal networks”. As might be expected, these attacks were followed by soaring premiums – by September 2021, cyber premium rates per million dollars of coverage had jumped more than 170% over the previous 12 months.
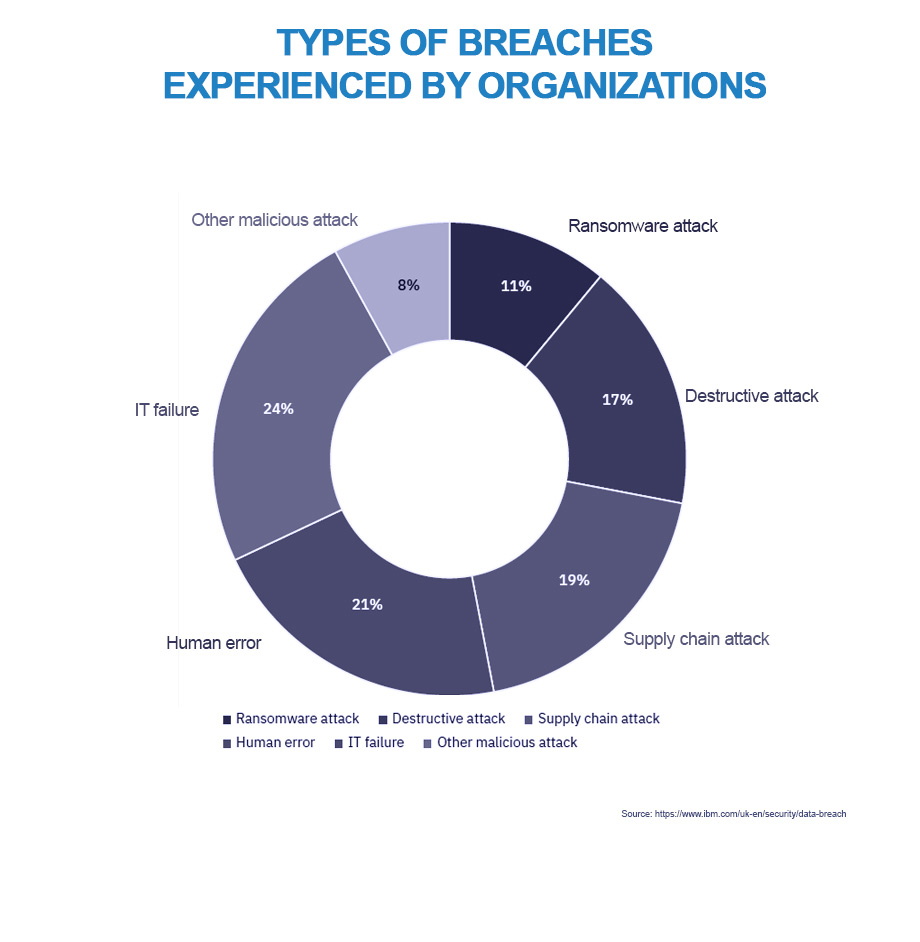
As organisations are beginning to discover, cyber threats are not only limited to ransomware.
According to the UK’s National Cyber Security Centre, techniques such as domain shadowing are far more widespread than previously imagined. Domain shadowing is a form of DNS hijacking whereby hackers compromise domain names in order to attack a domain’s owner, or for phishing, malware distribution or command and control operations. It is also used to harvest users’ credentials through fake login pages. Shadowed domains are hard to detect, because malicious subdomains can be created by stealth under compromised domain names. Victims of an attack can suffer huge reputational damage from a compromised domain because the subdomains created by an attacker can remain largely inconspicuous for long periods.
Palo Alto Networks’ Unit 42, a team of cyber and strategic security experts, conducted research that indicates that only a very small number of domain-shadowing incidents (200 out of every 12,000) are being correctly identified and marked as malicious by VirusTotal, the free web-based virus information aggregator established by Spanish security firm Hispasec Sistemas.
Target exposure
Over 50% of cyber-attacks are targeted at SMEs, and nearly 70% of small businesses have experienced at least one attempted cyber-attack in the last two years. Malware attacks, however, do not necessarily seek out specific industries or types of company; they are looking to exploit any weaknesses. “They are typically looking for low-hanging fruit,” says Aon, “which are the least secure organisations”. According to Beazley’s Risk & Resilience research, “mid-market clients, in particular, are struggling with what is being asked of them in terms of funding, budgeting for and repairing technology to keep pace with a range of cyber and technology risks”.
It is not just SMEs, however, that are exposed.
Aside from businesses large and small, cybercrime also affects critical infrastructure and supply chains, and the motivations behind such attacks are not exclusively economic. Hackers driven by ideological rationales, or “hacktivists”, often target businesses or government agencies that, for whatever reason, challenge their worldview. “The ideological hacker is a very worrisome one,” says Aon’s Erin Whitmore. “Malware [can be] repurposed so that a hacktivist can use it against a particular company, country or industry”.
Hacktivists are often motivated by a desire to cause economic or political instability, or both, by subverting democratic events and disrupting or destroying other processes or systems to further their ideological cause. Aside from the attack on Colonial Pipeline already mentioned, this was also evidenced by a foiled attempt to poison water supplies at a water-treatment plant in Florida in 2021.
As we have seen with Ireland’s healthcare system, healthcare and hospitals continue to attract criminal cyber-attacks. According to IBM’s “Cost of a Data Breach Report 2022”, healthcare was the highest cost industry for the twelfth year in a row for cyber intrusions and data theft. Although the average total cost of data breaches in 2021 was just over US$ 4 million, breaches in the healthcare industry cost an average of over US$ 9 million.
Authorities in USA, UK and Australia are reporting a large increase in the threat to critical infrastructure, including healthcare sites, utilities, food production networks and government agencies of all sizes, and the threat level is not expected to fade anytime soon, according to MunichRe.
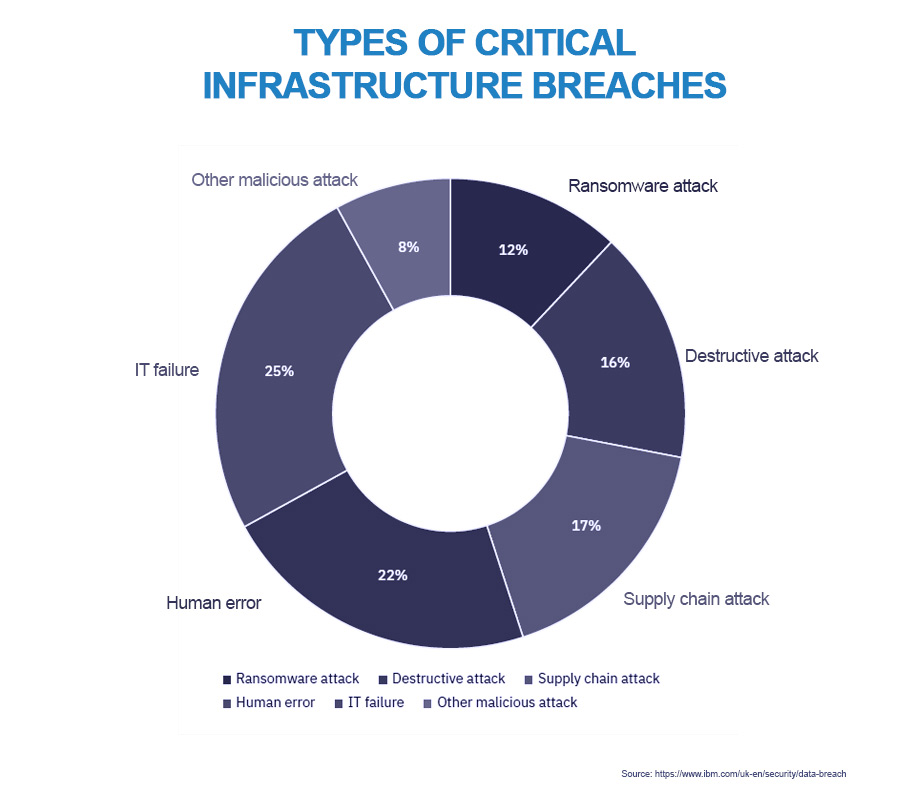
With a just-in-time global supply chain increasingly dependent on digitalisation and cloud services, supply-chain attacks can trigger what are known as accumulation scenarios. In such scenarios, just one effective attack can cause losses to multiple insureds. Industries and supply chains rely heavily on large numbers of diverse service providers for the software and hardware required by widespread digitalisation, and this often presents hackers with an opportunity to exploit gaps in protection. The result is heightened risk exposure.
The sheer scale of risk assessment and security standard management across a vast array of software and hardware components throughout entire supply chains can easily, it seems, open up a chink in the armour just long enough to cause widespread damage. As evidenced by last year’s attack on remote monitoring software provider Kaseya, even fleeting gaps in protection can be exploited to huge effect. In Kaseya’s case, hackers compromised around 1,500 of the company’s managed service provider (MSP) clients by infecting them with REvil ransomware, delivered by way of an automatic software update. This created havoc and disruption across multiple client organisations. As Kaseya began to understand the scale of the attack, the management team was forced to alert clients to widespread fake email notifications that purported to be Kaseya updates but turned out to be phishing emails with malicious links and attachments.
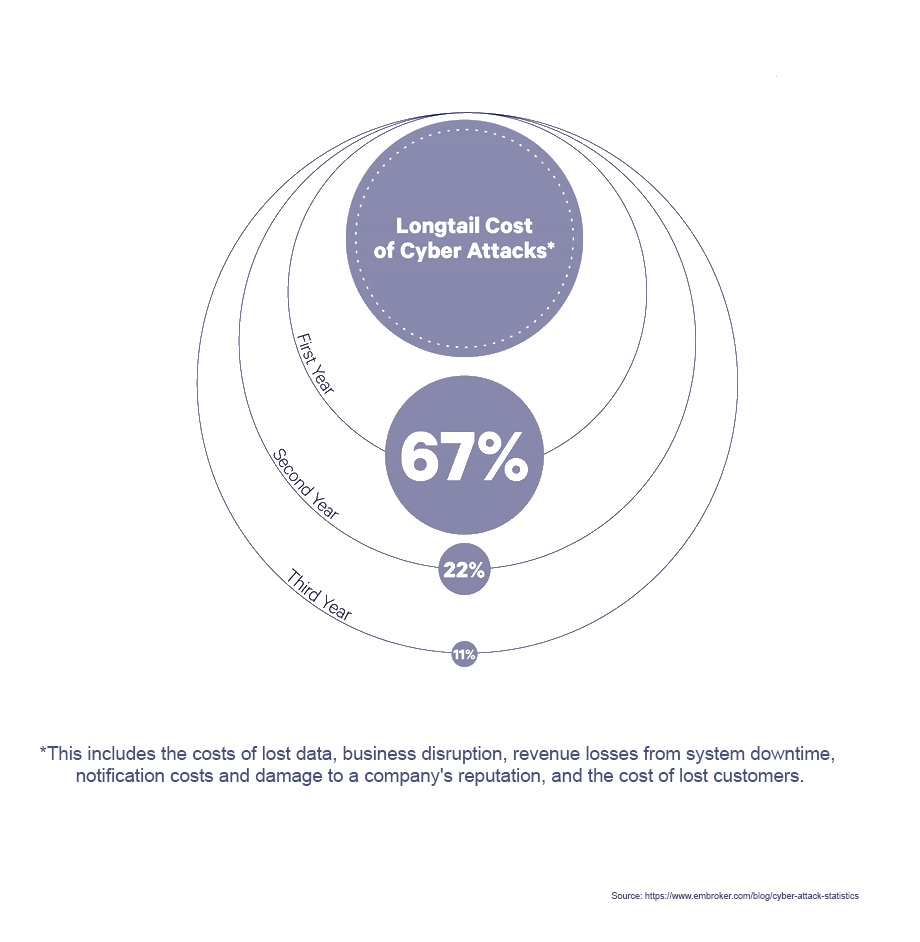
The cost of cybercrime has wide-reaching effects far greater than the dollar value reported. Although Cisco’s ‘2022 Cybersecurity Almanac’ puts the cost at more than US$ 10 trillion by 2025, cybercrime can affect its victims for many years after an attack; a combination of lawsuits, liability compensation and bad PR can prove fatal for businesses, and 60 percent of SMEs are forced to cease trading within as little as six months of a data breach or hack. The knock-on effects and human costs are almost impossible to calculate.
What can businesses do to protect themselves?
As public and private organisations attempt to mitigate the risk of cyber-attack, there are measures they can take to protect themselves, upgrade their cyber hygiene and improve their insurability. Cyber hygiene is, after all, a crucial step in improving insurability. As Beazley’s Risk & Resilience research points out, insurers are now more particular about which risks they write. Therefore, organisations will need to move beyond seeing cyber resilience as “just a box-ticking exercise”, says Beazley’s Aidan Flynn.
Business leaders should also be cautious of so-called “silent cyber”, in which possible but indeterminate cover may be contained under existing traditional policies. The problem with silent cyber is that it leads to considerable uncertainty as to what may or may not be covered in the event of an attack. Cyber-specific policies, on the other hand, offer support beyond financial protection; PR, reputational-damage limitation and 24-hour incident-response services such as IT forensics can all be mobilised within minutes of becoming aware of an attack. These are essential post-breach resources that SMEs in particular might struggle to deploy quickly enough, even if they had the resources.
The key message for public and private organisations is that cybersecurity begins at the top. As Cybersecurity Ventures’ Steve Morgan notes, the value of a company now is largely dictated by the strength of its cybersecurity and its resilience to cyber threats. “Someone should be in the boardroom,” Morgan says, “who will wave the red flag and get everyone else paying attention to the severity of cyber risks”.
The key word here is “everyone”. As mentioned above, over 80% of data breaches involve human error. Therefore, security awareness across an entire organisation is the first step in understanding its cyber-risk profile and risk exposure. In short, non-security staff need to be aware of how security issues relate to everyday tasks and processes.
With the cost of cyber-attacks and data breaches topping US$ 10 trillion by 2025, it is crucial to increase security awareness in light of increasing digitalisation. Accelerated digitalisation will lead to ever-growing numbers of mobile and IoT devices – the number of embedded networked sensors alone is expected to grow from 1 trillion today to 45 trillion in 20 years – and these will continue to grow more susceptible to malware and phishing emails. After all, when human error is responsible for over 80% of data breaches, any amount of increased security awareness among employees can only improve protection.
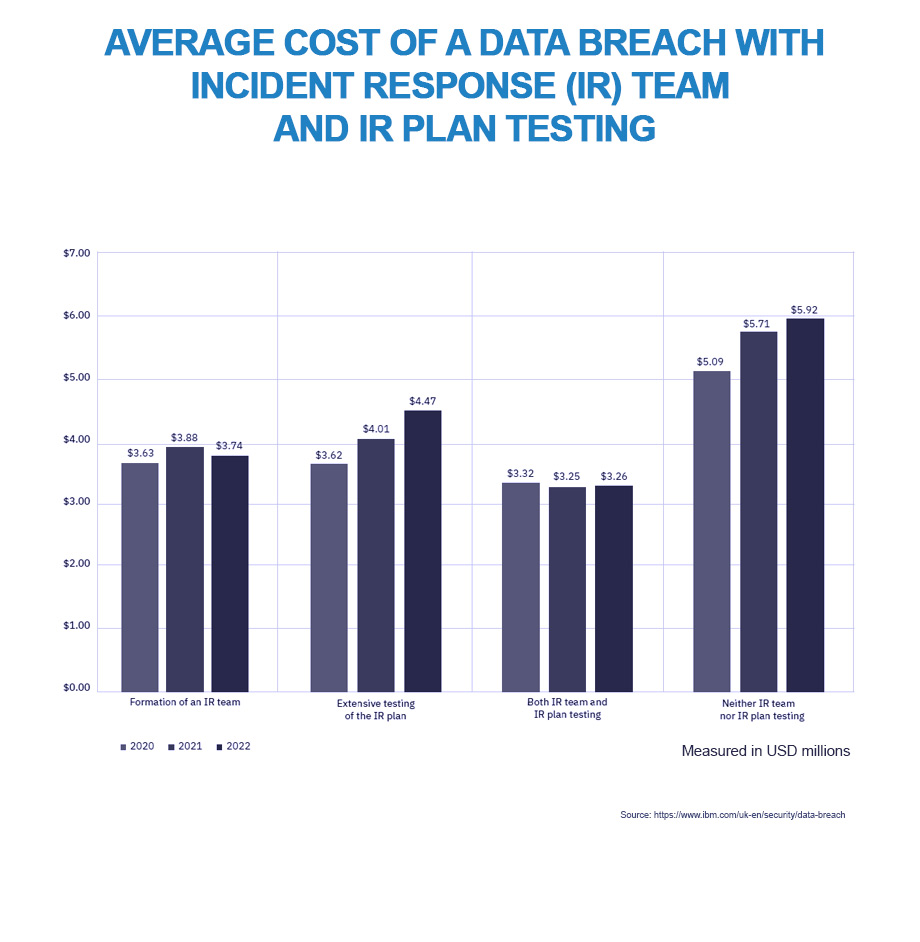
IBM’s “Cost of a Data Breach Report 2022” shows that companies with incident-response (IR) plans and IR teams that regularly tested those plans, achieved savings of almost 60% on the average cost of data breaches. As the report authors note, “the gap between the average data breach cost at organisations with both IR teams and IR plan testing and those with neither […] continued to grow [between 2020 and 2022]. Breaches at organisations with IR capabilities saw an average breach cost of US$ 3.26 million in 2022 compared to US$ 5.92 million at organisations without IR capabilities”.
Organisations that adopt a so-called “zero-trust” security model can limit access to certain data and thereby better protect it by clamping down on unauthorised access to sensitive data. The need for such a security model becomes ever more acute with the deployment of hybrid remote-work practices and off-site data storage with cloud providers.
Zero-trust security models are not yet widespread – IBM reports that only around 40% of companies surveyed have adopted the model – but organisations that have implemented and embedded zero-trust security showed cost savings from data breaches of US$ 1.5 million.
What might the future hold?
The insurance industry has a vital role to play in supporting businesses to navigate increasing digitalisation through unpredictable cyber risk, and insurers are well placed to help companies add value through cyber cover.
Digitalisation is transforming every part of the economy, but is, at the same time, dramatically increasing risk exposure across diverse and often hard-to-manage supply chains. Tailored cyber products are likely to help organisations meet the need for protection whilst allowing for profitability in the cyber insurance market.
As reported by MunichRe, many insurers are already helping companies develop cyber resilience through policy-holder risk assessment. This helps clients meet the preconditions necessary to access the cyber market. Indeed, there appears to be some enthusiasm within the insurance industry to change the way insurers assess insureds’ security risks and profiles. According to research by cybersecurity technology firm Panaseer, “nine out of 10 insurers believe it’s important for the industry to develop a consistent approach to analysing a customer’s cyber risk using accurate security metrics and measures”. Such approaches are already well advanced among investors, especially in the venture-capital space, where cybersecurity risk has become a key measure in assessing investment opportunities.
Following the attack in 2021 on the US Colonial Pipeline, governments have begun to respond to the threat of ransomware. It is expected that up to one-third of national governments worldwide could, by 2025, establish some form of regulation to curtail or outlaw ransomware payments to deter further growth in this area of cybercrime. Although still too early to tell, given the rapidly changing nature of cybercrime, it is possible that this may have a positive effect, and some cyber-security experts believe that cyber insurance cover is the single biggest determinant of whether a company falls victim to ransomware or not. Victim profiling by criminal groups based on the size of their cyber insurance cover, they claim, makes them prime targets for extortion.
Cybersecurity risk will constitute a major consideration in business deals, including mergers and acquisitions and vendor contracts, and potential partners’ cybersecurity profiles and resilience are likely to come under intense scrutiny by way of questionnaires, assessments and security ratings. Gartner predicts that by 2025, cybersecurity risk will emerge as the primary decider when considering and conducting third-party transactions in as many as 60% of all organisations.
The greatest threat in tomorrow’s world
As discussed above, cybercrime costs could exceed climate-change costs, yet few appreciate the true threat to global prosperity posed by cybercrime.
National lawmakers and the global insurance industry have a part to play in establishing cyber resilience standards to ensure the safety of expanding digitalisation, to protect the viability of businesses and safeguard the world economy from this massive and illicit transfer of wealth.
In order to support the transition to the new digital era, organisations & governments need to prioritise cyber risk as one of the main threats to economic and political stability going forward, requiring both appropriate and urgent action.




