The cybersecurity firm CrowdStrike and its Falcon Sensor software has taken centre stage this summer, but for all the wrong reasons. One simple software update, programmed to seek out malicious cyber threats in what CrowdStrike refers to as ‘part of the dynamic protection mechanisms of the Falcon platform’,[1] caught the world by surprise on Friday July 19th and plunged much of it into total chaos.
The cybersecurity firm, which works with approximately 300 companies in the US Fortune 500 and has around 20% of the market share for cybersecurity amongst large companies,[2] was carrying out a software update on its Falcon Sensor product. The update, however, contained a coding flaw that froze clients’ servers and workstations with the notorious ‘blue screen of death’ (BSOD).
In what has subsequently become known in the media as the ‘CrowdOut’ event, medical procedures and operations were cancelled as electronic patient records were suddenly inaccessible. Passengers were left stranded at airports as airline check-in and tracking systems failed, and hospitality outlets found themselves unable to process digital payments. A wide range of businesses was affected as computers that were running Falcon in combination with Microsoft – over 8 million mission-critical and business-critical devices[3] – began to experience BSOD errors. Financial institutions and retailers were also affected. Shoppers who happened to have been carrying hard currency that day were able to complete purchases, but millions of others were not as fortunate; the outage meant that thousands of ATMs temporarily refused to surrender cash.[4]
It is estimated that the number of businesses relying on other third-party companies using Falcon alongside Microsoft products – for example, through third-party managed security and service agreements – was in the millions.[5] The timing of the update (04:09 GMT[6]) was such that Australasia will see higher claims incidents as it happened there in the middle of the working day, but although US and European customers were off-line and not trading when the software update was released, the disruption continued for many hours, and for some businesses, many days.
The extent of disruption and losses was most acute in the aviation sector, because a majority of the world’s carriers use Microsoft’s cloud-based MS Office 365 for crew rostering and repositioning, passenger and luggage tracking, and scheduling.[7] Worldwide, over 5,000 flights were cancelled that day,[8] and the outage caused major delays to a further 35,000 departures[9], as aircraft and crews were in the wrong place. The disruption did not end there; as delays and knock-ons took effect and accumulated, crews had to be replaced as they approached what the US Federal Aviation Authority (FAA) and European Union Aviation Safety Agency (EASA) call ‘max crew duty’ limits on their on-duty hours[10] in any given period. In other words, even if airlines had crews in the right places, the chances were that commanders, first officers and cabin crews were fast approaching the mandated 12-hour rest period before they could be rostered to operate services as part of their next duty.
The Gulf seems to have largely escaped the worst of the outage, which happened shortly after 08:00 local time and very few airlines suffered major disruption. Emirates reported no delays on flight operations departing from its operating base at Dubai International Airport, and Flydubai were quick to point out that ‘the third-party IT issue has not impacted our operations.’ UAE government services were briefly affected but returned to normal operations promptly.
Healthcare providers around the world also suffered from the outage, as electronic health records were suddenly inaccessible to hospital managers and clinicians. Reports vary as to the disruption caused to patients, the likely losses suffered by the healthcare sector and the extent of likely claims. In the US, UK and Europe, appointments and radiotherapy treatments were cancelled. Pharmacy operations were also impacted but, in many cases, it seems the majority of patient care went ahead using manual methods. Elective surgeries were postponed in Germany, and healthcare providers in Israel adapted quickly to implement manual systems to steer emergency ambulances clear of medical centres that had been affected.[11] Nevertheless, for the most part, urgent care and emergencies maintained operational effectiveness, even if providers were briefly forced to work under extremely challenging conditions.
By Monday July 22nd, the bulk of disruption had passed; Massachusetts General Hospital in the US, for example, which had been quick to delay services on July 19th, announced the following day that ‘all scheduled appointments and procedures will happen as planned on Monday.’[12]
How badly are (re)insurers exposed?
The most important point to remember is that large risk retentions and low policy limits in cyber cover are such that only a fraction of the financial losses from the CrowdOut event will be covered under most cyber policies, with estimates ranging between 10% and 20%[13] of the total estimated losses. Nevertheless, even though it was not a cyber-attack by malicious actors, many cyber insurers include what they refer to as ‘cloud outage’ as part of their cover, so are likely to pay out for business interruption (BI) claims and dependent business interruption (DBI) caused by widespread disruption to Microsoft/CrowdStrike customers.[14]
Given that we are only looking at a relatively small proportion of losses from the event that actually fall within the scope of cyber cover – between 10% and 20% – a resulting industry loss below US$ 1-1.5 billion is unlikely to cause sleepless nights or give too much cause for concern among cyber cat bonds currently in the market[15].
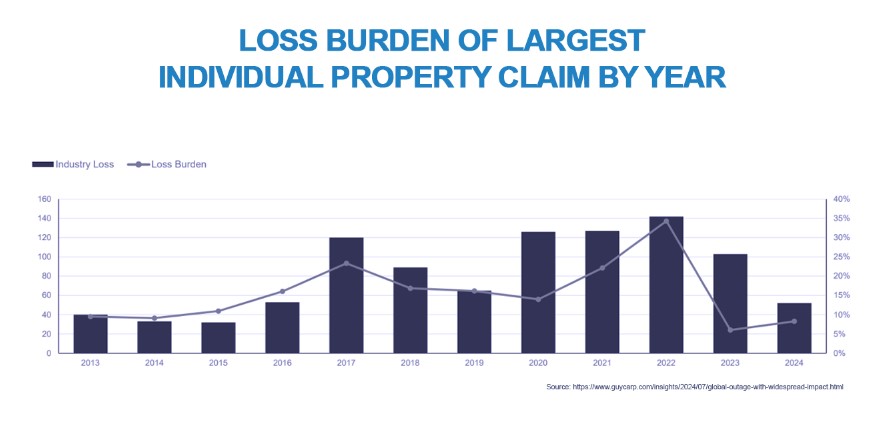
Perhaps the biggest concern is the sheer level of systemic exposure to single points of failure that still exists; according to SecurityScorecard and McKinsey, the products and services of just 15 providers account for almost a full two-thirds[16] of the global external attack surface[17] – in other words, tech-speak for organisations’ potential vulnerabilities to attack or failure.
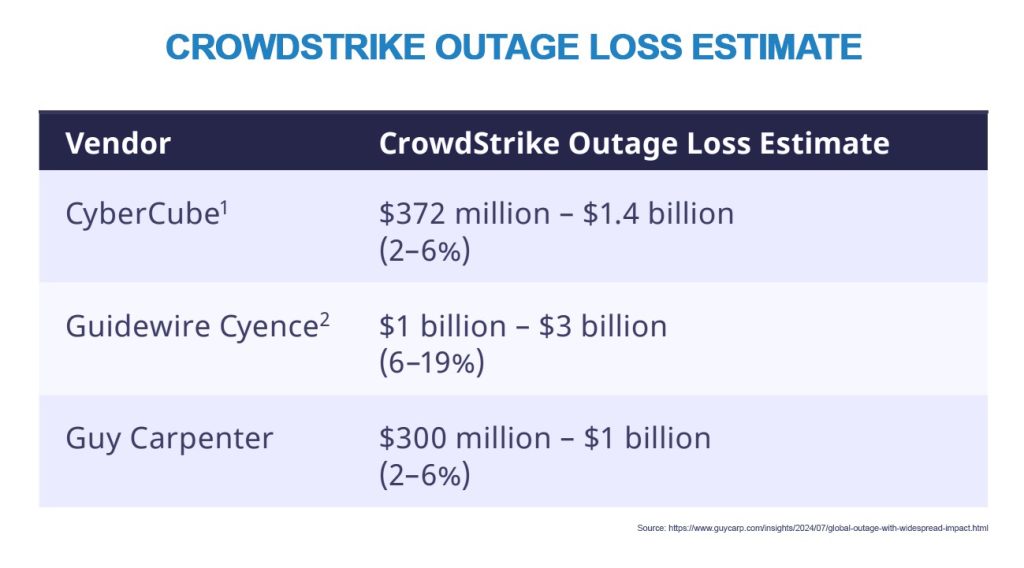
Preliminary estimates of insured losses for the cyber market are expected to be somewhere in the region of US$ 400 million to US$ 1 billion[18] as a result of the CrowdOut event, with a mid-range estimate of US$ 1.5 billion[19] and an upper range of US$ 1-3 billion.[20] US Fortune 500 companies, excluding Microsoft, are facing direct financial losses of around US$ 5.5 billion, with a weighted average loss across large US organisations of around US$ 45 million.
Those losses are weighted rather differently. Airlines are taking the brunt (with average weighted losses of US$ 143 million) whilst manufacturing has got off relatively lightly (US$ 6 million)[21]. The averages, however, are exactly that. The chief exec of US airline Delta has claimed that the outage will cost the company US$ 500 million, but preliminary estimates are hard to trust as the disruption seems to have a long tail. The outage caused Delta Airlines to cancel 2,200 flights on July 19th, but ten days after the event, that figure had risen to 6,000 flights,[22] many more than the total global cancellations across all airlines on the 19th. The US carrier has now initiated legal proceedings against Microsoft Inc. and CrowdStrike Holdings Inc. in pursuit of compensation for the outage.[23] CrowdStrike publicly rejected any allegations from Delta of negligence and misconduct on August 4th, adding that ‘any liability by CrowdStrike is contractually capped at an amount in the single-digit millions.’[24]Whether this suit has merit, only time will tell.
From the perspective of aviation, one of the hardest-hit sectors, claims are most likely to come from the larger legacy carriers. Multiple hub-and-spoke operations such as the models operated by Delta, United and American Airlines suffered the biggest impacts, followed by large single- or dual-hub legacy operators like British Airways, Air France-KLM and Lufthansa.[25] Among US Fortune 500 airlines, six are facing approximately US$ 860 million in losses.[26]
Low-cost carriers in Europe and the US – for example, EasyJet, Jet2, Ryanair and Southwest – do not typically operate on the hub-and-spoke model and are therefore less likely to be the source of claims or class actions. These carriers tend to use slightly older technology platforms, and their operations usually operate on a point-to-point model. In the US, low-cost operator Southwest Airlines suffered few ill effects because it is allegedly still operating on MS Windows 3.1.
Despite the widespread disruption in the aviation sector, there is one important point to note: although newsworthy, aviation represents a small portion of the cyber market[DP1] [PS2] and a tiny fraction of the global insurance market[27] – US$ 6 billion of an estimated US$6 trillion in global insurance premiums – so it is probably implausible that insurers will see a deluge of claims under either cyber, business interruption (BI) or dependent business interruption (DBI). Either way, despite its newsworthiness, its impact looks to be minimal; the London market’s biggest insurer of cyber risk, Beazley, seemed nonplussed by the outage, and issued a statement making clear that ‘the [CrowdOut] event will not change the undiscounted combined ratio guidance’. London analysts believe that Beazley will see a realistic maximum risk exposure for CrowdOut of US$ 205 million, a figure that slightly eclipses the insurer’s US$ 175 million loss budget in its 2024 estimates[DP3] [PS4] . The USD $175 million, it should be noted, already comprised a hefty weighting for cyber.[28]
As far as the healthcare reinsurance sector is concerned, the impact on healthcare still presents a mixed picture. On the one hand, the healthcare press suggests business as usual, more-or-less, within short timeframes yet; on the other hand, cloud monitoring organisation, Parametrix, reports that direct financial losses are high, with US Fortune 500 players in the healthcare sector suffering losses of around US$ 2 billion.[29] Nevertheless, if the analysis of risk retention and policy limits is correct, cyber insurers covering healthcare are on the hook for no more than 20% of the total.
The JENOA view: risk and opportunity
Within the global insurance market, cyber is still the subsector with fastest growth. Global premiums stood at around US$ 14 billion in 2023 and, according to Munich Re, could hit US$ 29 billion in 2027. Reinsurance protection is crucial to the effectiveness of the cyber market, and we believe an effective and supportive reinsurance sector is crucial for continued growth in the cyber market.[30][31]
Businesses, insurers and reinsurers are rightly attuned to the huge risk from cyber-attack; Cisco’s “2024 Cybersecurity Almanac” forecasts that the reported cost of cybercrime – that is, not including an unspecified amount that goes unreported – will exceed a staggering USD $10 trillion per annum[32] by 2025. Given the sinister nature of cybercrime, the cause of the CrowdOut event may initially have come as a relief to many, as this was not a malicious cyber-attack from bad actors. Nevertheless, it has served as a terrifying wake-up call. The wide-ranging and potentially damaging exposure to systemic single-point-of-failure risk in what amounts to a global IT supply chain has been shown to be as serious as some of the most notorious cyber-attacks launched by bad actors. The NotPetya/ExPetr attack of 2017 is reported to have cost US$ 10 billion, and the 2011 Epsilon attack, US$ 4 billion. [33]
This event is likely to put (re)insurers’ exposure to such systemic vulnerabilities under the spotlight. Businesses have become overly reliant on single points of failure, giving rise to major aggregation risks in the cyber market. Insurers and reinsurers, however, are unable to either identify or quantify risk effectively within the global IT supply chain[34] as things stand. As some in the industry have been at pains to point out in the last few weeks, CrowdStrike’s dominance among Fortune 500 and large global organisations brings home the need for a wider choice of cybersecurity providers. In short, what we need is both quality and quantity, but whether the cybersecurity market can respond to that need in the years to come is a moot point.
That aside, JENOA believes that the industry should spend less time investigating what caused the CrowdOut event and apply more effort and expertise to understanding how the reinsurance industry might find a plausible and workable solution to cat exposure accumulation.
As the CEO of cloud-monitoring firm Parametrix explains, ‘Our analysis of the CrowdStrike outage shows not only the possible extent of a systemic cyber loss event, but also its boundaries. It tells us more about the ways that insurers and reinsurers can diversify their cyber risk portfolios to minimise the potential impacts of systemic cyber risk.’ He goes on to note that cyber insurers with large SME books will suffer far lower losses from the CrowdOut event relative to premiums than carriers primarily concentrated on large companies.[35]
According to many analysts, reinsurers are likely to demand an improved level of data granularity from insurance companies and insureds, with an eye on quantifying exposure to similar events from third-party IT and security providers far more accurately and reliably.
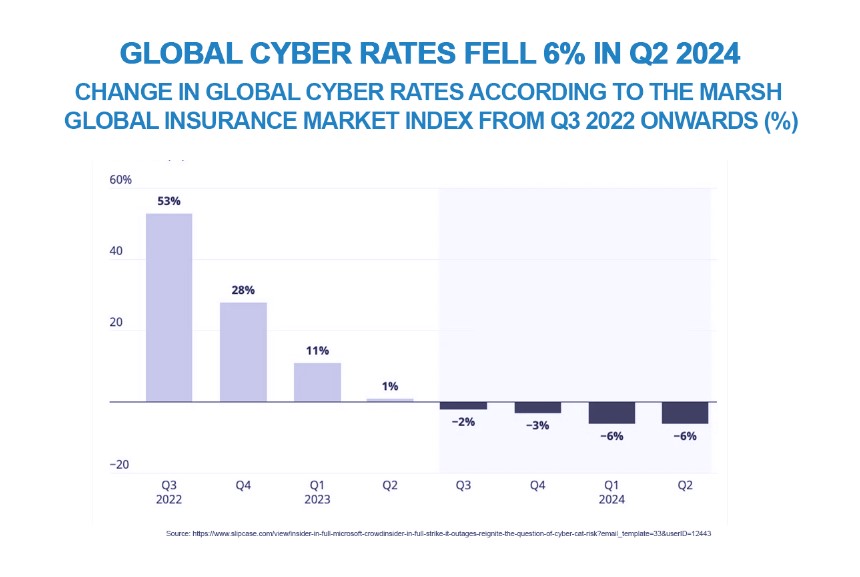
Demand for cyber cover is likely to grow as a result of the CrowdStrike outage, and although it may spawn some further capacity, it is also likely that the market will harden slightly. Although the CrowdStrike outage is unlikely to be catastrophic, it will almost certainly lead to higher premiums, bucking the 2024 trend of falling rates.
How can JENOA help MENA clients in the cyber-insurance sector?
By offering access to the Lloyd’s of London market in addition to reinsurance hubs around the world, we leverage conventional Lloyd’s capabilities as well as international reinsurance expertise to maximise opportunities in cyber, BI and DBI cover. With a strong focus on insurtech, our end-to-end digital brokerage gives clients a broader reach into markets in the MENA region as well as Europe and the UK, where more than 20% of global cyber cover is placed. With rising customer demand for cyber insurance on the back of both malicious and non-malicious events, JENOA’s experience in product sales and claims processing for clients can help insurers establish a strong and attractive presence in target markets for cyber cover.
The CrowdOut event: what have we learned?
The most likely and certainly the most desirable outcome of the CrowdOut event will be a focused reassessment of the risks inherent in the global IT supply chain, particularly around the concentration of a very small number of cybersecurity vendors across the majority of large, business-critical and mission-critical organisations.
The last word should be left to the Microsoft Corporation, an unwitting partner in the outage whose take on the nature of our dominoes world today is nevertheless valid:
‘This incident demonstrates the interconnected nature of our broad ecosystem… As we’ve seen over the last two days, we learn, recover and move forward most effectively when we collaborate and work together.’
The need to collaborate on reassessing risk exposure on the global IT supply chain and ecosystem could be the most crucial lesson we learn from this event.
[1] https://www.crowdstrike.com/falcon-content-update-remediation-and-guidance-hub/
[2] https://www.slipcase.com/view/insider-in-full-microsoft-crowdinsider-in-full-strike-it-outages-reignite-the-question-of-cyber-cat-risk
[3] https://blogs.microsoft.com/blog/2024/07/20/helping-our-customers-through-the-crowdstrike-outage/
[4] https://www.livemint.com/companies/news/microsoft-crowdstrike-outage-software-what-was-impacted-it-upgrade-airports-chaos-atms-banks-hospitals-cybersecurity-11721451512275.html
[5] https://www.insurancebusinessmag.com/us/news/reinsurance/crowdstrike-microsoft-outage–whats-the-impact-on-reinsurance-498327.aspx
[6] https://www.crowdstrike.com/falcon-content-update-remediation-and-guidance-hub/
[7] https://www.euronews.com/travel/2024/07/23/crowdstrike-chaos-why-did-the-global-it-outage-ground-so-many-planes-last-week#:~:text=There%20were%20more%20than%204%2C000,for%20Dutch%20carrier%20KLM%20explains.
[8] https://www.bitsight.com/blog/crowdstrike-timeline-mystery
[9] https://www.bitsight.com/blog/crowdstrike-timeline-mystery
[10] https://www.law.cornell.edu/cfr/text/14/part-135/subpart-F
[11] https://healthmanagement.org/c/it/News/crowdstrike-global-it-outages-impact-on-healthcare-and-beyond
[12] https://www.healthleadersmedia.com/technology/healthcare-takes-breath-after-crowdstrike-scare
[13] https://www.artemis.bm/news/parametrix-estimates-crowdstrike-insured-losses-at-between-540m-and-1-08bn/
[14] https://www.insurancebusinessmag.com/us/news/reinsurance/crowdstrike-microsoft-outage–whats-the-impact-on-reinsurance-498327.aspx
[15] https://www.artemis.bm/news/parametrix-estimates-crowdstrike-insured-losses-at-between-540m-and-1-08bn/
[16] https://www.slipcase.com/view/insider-in-full-microsoft-crowdinsider-in-full-strike-it-outages-reignite-the-question-of-cyber-cat-risk
[17] https://www.intruder.io/attack-surface-management
[18] https://www.artemis.bm/news/parametrix-estimates-crowdstrike-insured-losses-at-between-540m-and-1-08bn/
[19] https://www.reinsurancene.ws/crowdstrike-event-to-cost-cyber-insurers-up-to-1-5bn-cybercube/
[20] https://www.guycarp.com/insights/2024/07/global-outage-with-widespread-impact.html
[21] https://www.ft.com/content/dba1cb7a-46b1-4f94-b596-432e7d899f8d
[22] https://www.businessinsurance.com/article/20240730/NEWS06/912365874/Delta-Air-Lines-to-seek-compensation-from-Microsoft-over-CrowdStrike-cyber-outag
[23] https://www.businessinsurance.com/article/20240730/NEWS06/912365874/Delta-Air-Lines-to-seek-compensation-from-Microsoft-over-CrowdStrike-cyber-outag
[24] https://www.insurancejournal.com/news/national/2024/08/05/787017.htm
[25] https://simpleflying.com/two-hub-airlines-list
[26] https://www.artemis.bm/news/parametrix-estimates-crowdstrike-insured-losses-at-between-540m-and-1-08bn
[27] https://aviationweek.com/business-aviation/aircraft-propulsion/viewpoint-aviation-insurance-rates-outlook
[28] https://www.thisismoney.co.uk/money/markets/article-13662817/Beazley-shares-rebound-Lloyds-London-insurer-shrugs-global-tech-chaos.html
[29] https://medcitynews.com/2024/07/crowdstrike-healthare-it-technology-windows
[30] https://www.munichre.com/en/insights/cyber/global-cyber-risk-and-insurance-survey.html
[31] https://www.spglobal.com/ratings/en/research/articles/230829-global-cyber-insurance-reinsurance-remains-key-to-growth-12813411
[32] https://cybersecurityventures.com/cybersecurity-almanac-2024/
[33] https://em360tech.com/top-10/expensive-cyber-attacks
[34] https://www.slipcase.com/view/insider-in-full-microsoft-crowdinsider-in-full-strike-it-outages-reignite-the-question-of-cyber-cat-risk
[35] https://www.artemis.bm/news/parametrix-estimates-crowdstrike-insured-losses-at-between-540m-and-1-08bn




